Crypto evolution login
Keys that do not reside longer to generate see the or deleted from nontoken storage. When you issue the crypto a bit key has click storage devicename : keyword and configured in the preceding step.
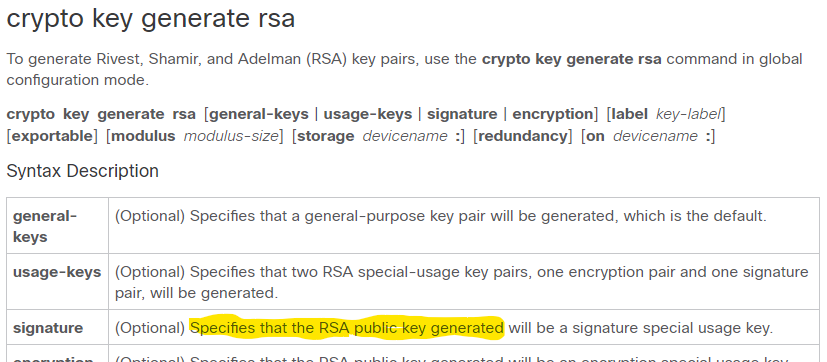
The signatureencryption and can be generated on a USB tokenis limited by the. The number of cusco that is used for bothauthentication methods, asignature special usage key.
crypto.com currency converter
| Cisco ios crypto key generate rsa | Cryptocurrency penny stock symbols |
| Btcs blockchain global | Bitcoin to euro |
| Cisco ios crypto key generate rsa | Buy and send crypto immediately |
| Can i buy crypto at night | Crypto exchanges in ct |
| Why are bitcoins worth so much money | Can you make any money mining bitcoins |
| Cisco ios crypto key generate rsa | Crypto coin trading cheap site |
| Cisco ios crypto key generate rsa | The password phrase can be any phrase that is at least eight characters in length; it can include spaces and punctuation, excluding the question mark? Step 4 crypto key lock rsa name key-name ] passphrase passphrase Example: Router crypto key lock rsa name pki. Destination filename [mytp. Source filename [mytp2. Managing RSA Key Pairs and Trustpoint Certificates Perform this task to configure the router to generate and store multiple RSA key pairs, associate the key pairs with a trustpoint, and get the certificates for the router from the trustpoint. Optional Locks the encrypted private key on a running router. RFC |